Наши инструменты отслеживают миллионы рекламных кампаний в нативной рекламе, push, pop и TikTok.
НачатьRunning non-compliant ad campaigns is nothing new. Many online advertisers try to skirt the rules established by ad-networks to run campaigns that are not permitted by that ad-network. We see many examples of such campaigns on a daily basis on our spy platform.
The most commonly employed technique involves disguising the ad copy with text and images that don't raise any flags. This is followed by creating a fake or an innocuous landing page that is shown to the compliance team while directing the traffic to the actual money making page to the majority of audience. This is referred to as cloaking within advertising community.
Let's look at a hypothetical example. Online gambling is illegal in the United States. Therefore, an advertiser is prohibited from showing gambling ads to US audience as it is illegal. There are many offshore online gambling platforms that are looking for US based clients. So either they themselves or their affiliates will try to run such ad campaigns using cloaking techniques.
One of the earliest cloaking technique involved showing a compliant landing page during the campaign approval process and the URL was then redirected to a non-compliant page after the campaign was approved. As you can imagine, such a technique is very easy to detect and black-hat advertisers started coming up with more sophisticated techniques. This can include identifying "suspicious" traffic using visitor IP address, looking at http headers for inconsistencies, running javscript checks to see if the traffic is originating from a mobile device or an emulator etc.
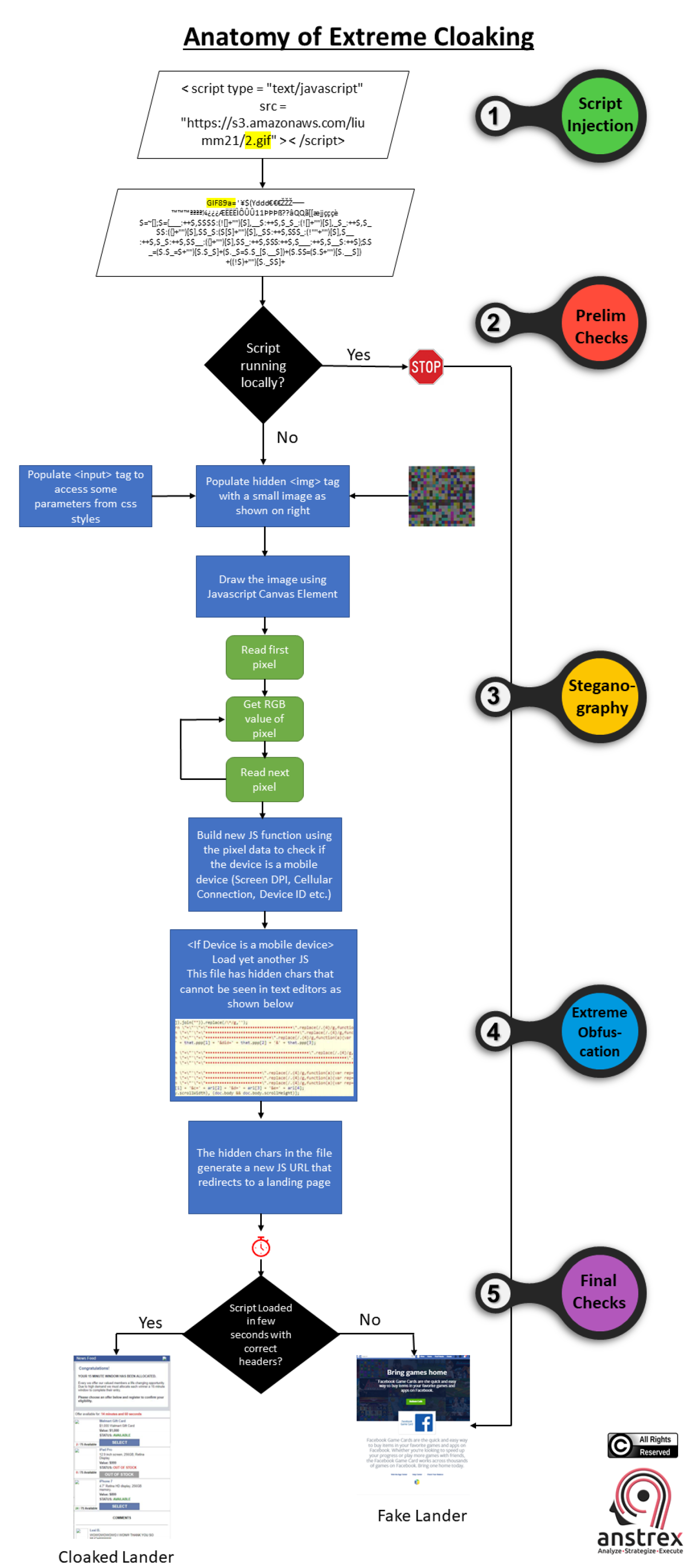
In this article, we are going to reveal one of the most complex and frankly jaw dropping cloaking technique that was first revealed by folks at bidfilter. It consists of multiple steps and checks that include some fascinating methods such as steganography, extreme obfuscation and clever javscript injection.
Before we detail the steps, let's take a look at the flow-chart below that makes it easier to understand the entire process:


Below are the links for the original whitepaper from bidfilter and high resolution pdf of the flow-chart, if you are interested.
White Paper: Original Whitepaper from BidFilter
Flowchart: High Resolution Flowchart in PDF format
As the author of the whitepaper noted, this by far is the most extreme example of the malicious ad serving that they have ever seen. I think it is safe to assume that this is not the last time we will see this. Ad-networks will have to step up their game if they are serious about fighting this kind of spam.
Получайте лучшие конверсионные лендинги каждую неделю на свою почту.
Нету
Понимание реакции потребителей на рекламные публикации заключается не только в отслеживании отметок «нравится» и репостов, но и в глубоком погружении в психологию, которая лежит в основе вовлеченности и решений о покупке.
Dan Smith
7 минянв. 21, 2025
Кейc
TikTok emerged как мощная рекламная платформа для предприятий электронной коммерции, стремящихся увеличить продажи и расширить свою клиентскую базу. Это исследование из Перу демонстрирует огромный потенциал TikTok для предприятий электронной коммерции.
Kulwant Nagi
7 миниюл. 14, 2024
Избранное
Jairene Cruz
7 минапр. 25, 2024